Some Centered Text
Scope Call
Hands-On Assessment
Exploit Vulnerabilities
Submit Professional Report
Remediation Call

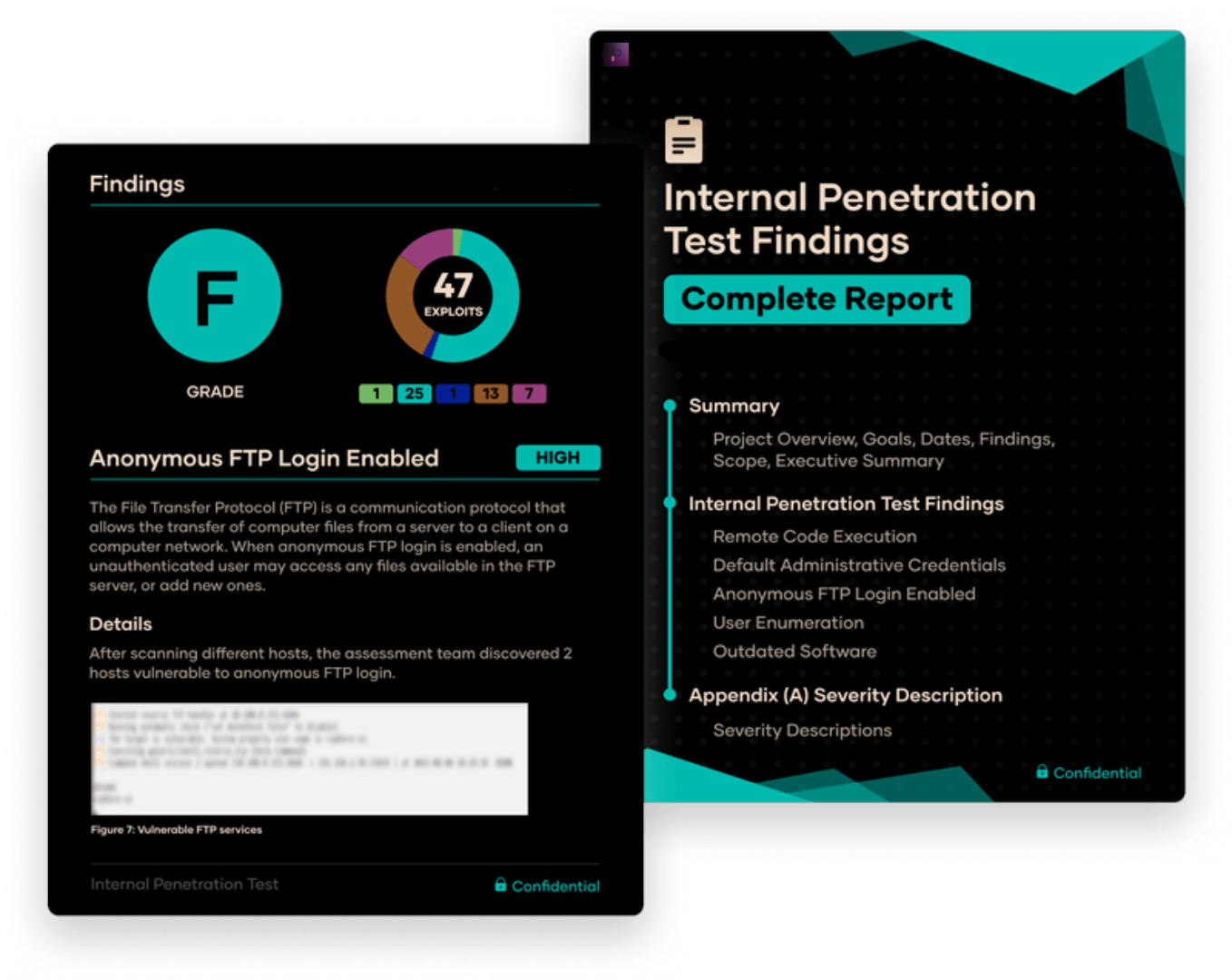

SOC 2, HIPAA, PCI DSS, ISO Standards, HITRUST, NIST, and CIS Compliance.

Full Pentest Reports Delivered Faster and More Effectively Than Anyone Else

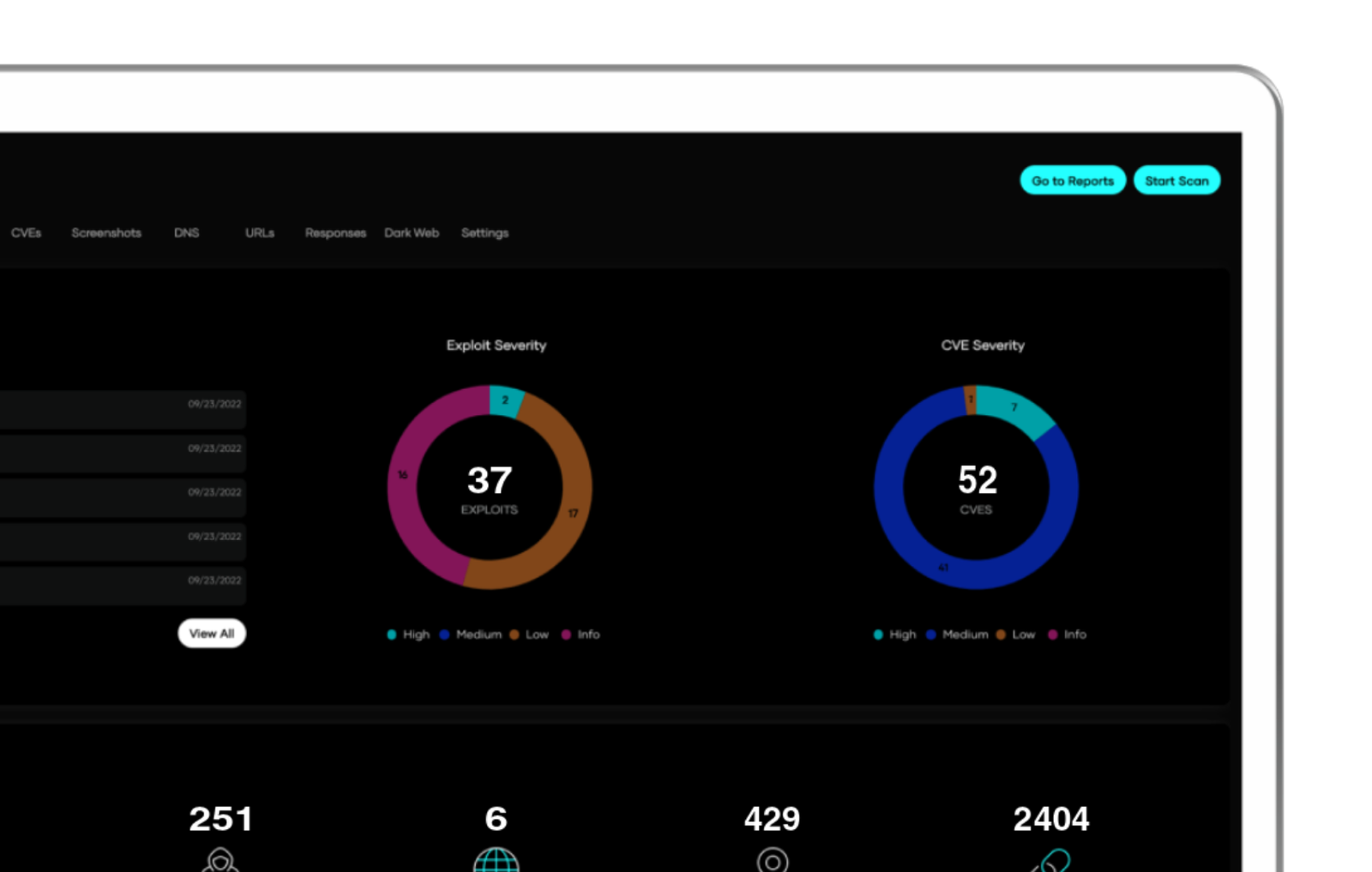
Regular Actionable Evaluations to Maintain Your Protection

814 Broadway Unit 1B, Newark, NJ 07104